
Detect and Prevent Fraudulent Transactions to Protect Your Customers
Foundation of Our Approach
Businesses risk falling victim to increasingly sophisticated fraud attacks. Fraud is a continuous battle and without real-time detection technologies, the financial impact of these activities may multiply. Therefore fraud identification in real-time helps build customer trust, enhance operational efficiency, and ensure compliances are in place. In this use case, we will showcase how integrating a bot detection system that utilizes Behavioral Analytics, CAPTCHA Systems, and AI/ML Models to differentiate between genuine users and automated bots during the registration process can prove to be beneficial to most businesses.

Key Elements Behind the Process
- Behavioral Analysis: Analyze user interactions, such as typing speed, mouse movements, and click patterns, to identify anomalies.
- CAPTCHA Systems: Implement challenges like image recognition or mathematical problems to filter out automated bots.
- Rate-Limiting and Honeypots: Monitor traffic to detect and block multiple rapid registration attempts and use honeypots to trap bots.
Fraud detection systems are always a work in progress. And as the complexities of committing fraud become more sophisticated, the need for intelligent strategies to prevent it has also grown. This diagram illustrates a Fraudulent Account Creation Detection System using various AWS services to protect and monitor traffic, block suspicious users, and analyze logs for improved security.
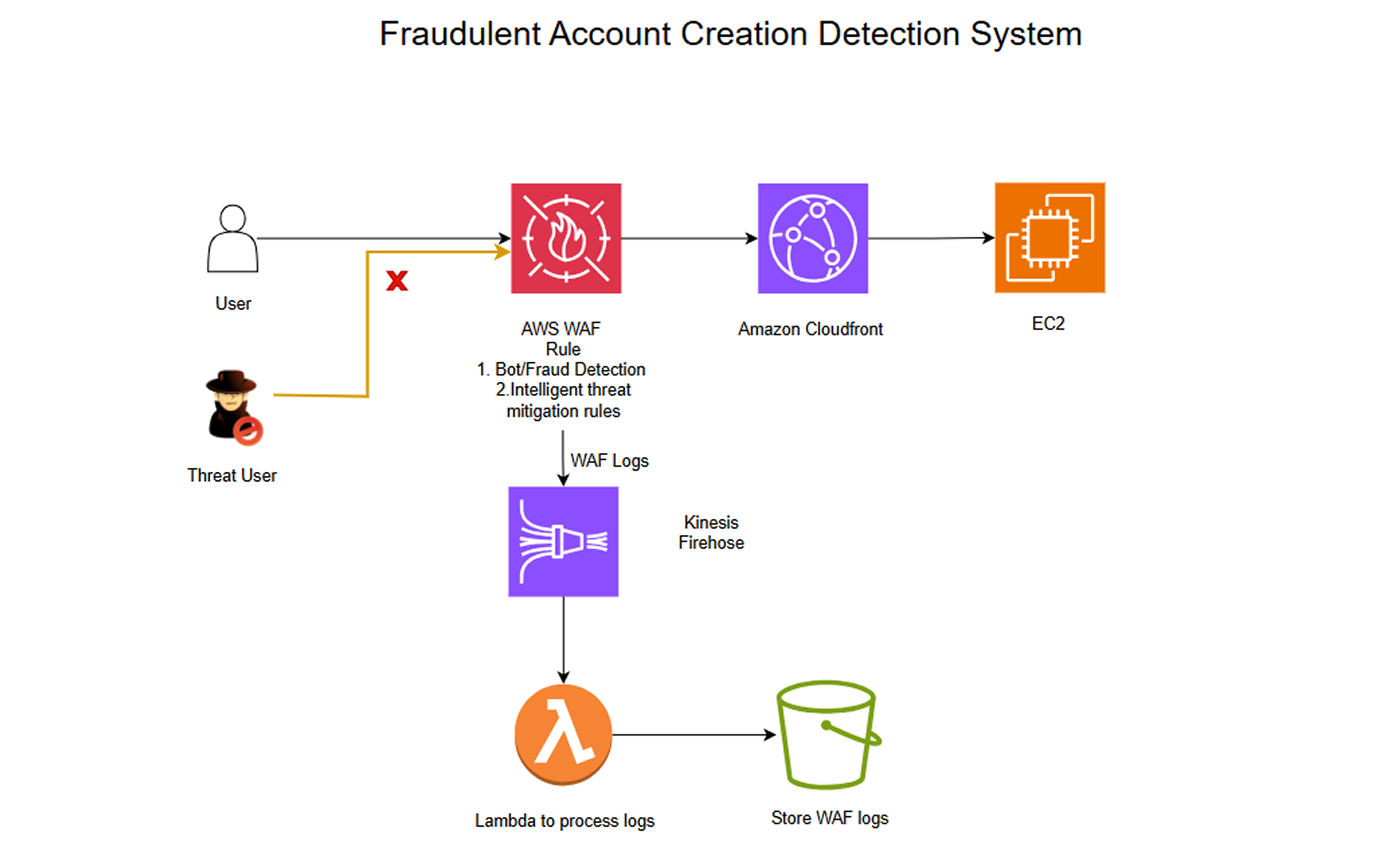
In this use case, we have broken down the components of the system and explained how they work together.
Detailed Breakdown of the Process
- User: Represents legitimate users attempting to access your system
- Threat User: Represents potentially malicious users, such as bots or attackers trying to create fraudulent accounts.
- AWS WAF (Web Application Firewall): The central component of this architecture protects the application by applying rules for bot and fraud detection, intelligent threat mitigation based on traffic patterns, and blocking suspicious requests while enforcing rate limits.
- Amazon CloudFront: A Content Delivery Network (CDN) that serves content with low latency, efficiently distributes traffic, and ensures secure delivery to application endpoints.
- Amazon EC2: Hosts the backend application or service, which processes valid requests.
- WAF Logs: Logs all activity, including blocked and allowed traffic.
- Amazon Kinesis Data Firehose: Streams WAF logs in near real-time for further analysis and processing.
- AWS Lambda: Processes WAF logs to extract insights, generate alerts, and provide flexibility in customizing log handling and automation.
- Amazon S3: Stores processed WAF logs for long-term storage, audit, and compliance.
How It Works
- Users and Threat Users send requests to the system.
- Requests are routed through AWS WAF, where rules are applied to detect and block malicious or suspicious traffic.
- If a request matches a fraud detection rule, AWS WAF blocks it.
- If the request is valid, it passes through CloudFront to reach EC2 for processing.
- AWS WAF generates logs for all requests.
- Logs are streamed via Kinesis Data Firehose to AWS Lambda, which processes them for analysis.
- Processed logs are stored in Amazon S3 for long-term use.
How It Gives Your Operations the Competitive Edge
- Enhanced Security: Protects your application from bots, malicious users, and fraudulent activities, reducing the risk of data breaches and account misuse.
- Improved Performance: By filtering traffic at AWS WAF and distributing valid traffic via CloudFront, your application avoids overloading backend systems, improving response times for legitimate users.
- Scalable and Reliable: The architecture scales automatically to handle spikes in traffic while maintaining availability.
- Real-Time Insights: Log processing with Kinesis Firehose and Lambda provides near real-time insights, enabling quick responses to emerging threats.
- Cost Optimization: By blocking malicious traffic at the WAF level, the system prevents unnecessary processing by backend resources, saving operational costs.
- Regulatory Compliance: Long-term storage of logs in Amazon S3 helps meet compliance requirements for auditing and reporting.
This system not only strengthens your application's security posture but also optimizes operations, improves user experience, and builds trust among your customers. Connect with our experts today to learn more!